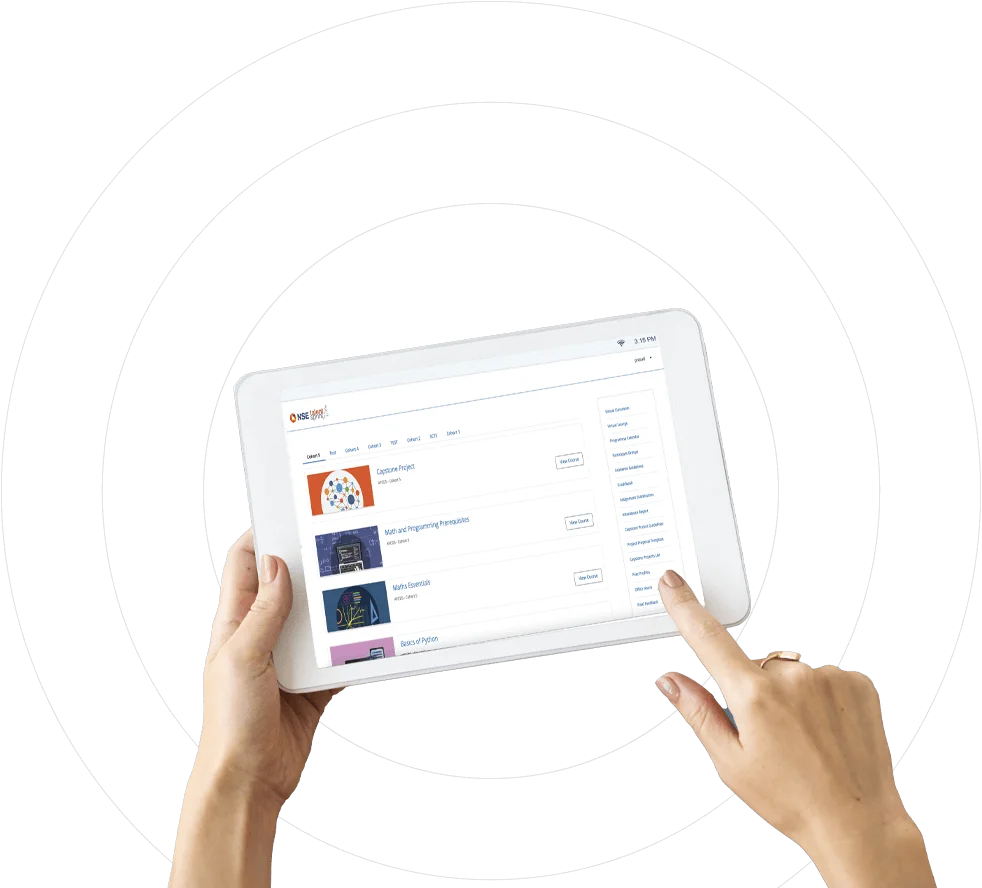
Elevate your Cyber Defense Game
e-Masters in Cyber Security
Build capabilities to combat an evolving threat landscape. Join the next generation of Cyber Security professionals with IIT Kanpur online masters degree program. Study with industry experts, develop hands-on skills and stay ahead in the field.

 coding knowledge
coding knowledge
is mandatory
- No GATE Score required
- IIT Kanpur Alumni Status





 Manindra Agrawal
Manindra Agrawal Sandeep K. Shukla
Sandeep K. Shukla Urbi Chatterjee
Urbi Chatterjee Debapriya Basu Roy
Debapriya Basu Roy Amitangshu Pal
Amitangshu Pal Debadatta Mishra
Debadatta Mishra Adithya Vadapalli
Adithya Vadapalli Angshuman Karmakar
Angshuman Karmakar Priyanka Bagade
Priyanka Bagade
 Live Interactive Sessions
Live Interactive Sessions Projects
Projects  Online Examination
Online Examination Campus Visit
Campus Visit
 Education loan avail from
Education loan avail from